i recently updated and upgrade parrot and now i am unable to use Fern Wifi Cracker.I tried running from menu but it would just ask me password and not open it so i tried running from terminal then i got this error
Please help me!!!Same here after
sudo parrot-upgrade
sudo apt install fern-wifi-cracker
┌─[a-man@parrot]─[~]
└──╼ $sudo fern-wifi-cracker
[sudo] password for a-man:
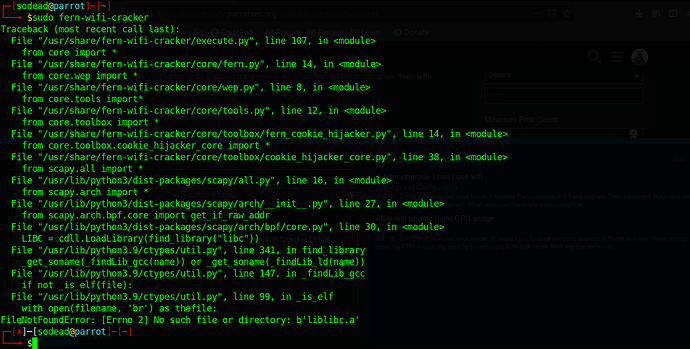
Traceback (most recent call last):
File “/usr/share/fern-wifi-cracker/execute.py”, line 107, in
from core import *
File “/usr/share/fern-wifi-cracker/core/fern.py”, line 14, in
from core.wep import *
File “/usr/share/fern-wifi-cracker/core/wep.py”, line 8, in
from core.tools import*
File “/usr/share/fern-wifi-cracker/core/tools.py”, line 12, in
from core.toolbox import *
File “/usr/share/fern-wifi-cracker/core/toolbox/fern_cookie_hijacker.py”, line 14, in
from core.toolbox.cookie_hijacker_core import *
File “/usr/share/fern-wifi-cracker/core/toolbox/cookie_hijacker_core.py”, line 38, in
from scapy.all import *
File “/usr/lib/python3/dist-packages/scapy/all.py”, line 16, in
from scapy.arch import *
File “/usr/lib/python3/dist-packages/scapy/arch/init.py”, line 27, in
from scapy.arch.bpf.core import get_if_raw_addr
File “/usr/lib/python3/dist-packages/scapy/arch/bpf/core.py”, line 30, in
LIBC = cdll.LoadLibrary(find_library(“libc”))
File “/usr/lib/python3.9/ctypes/util.py”, line 341, in find_library
_get_soname(_findLib_gcc(name)) or _get_soname(_findLib_ld(name))
File “/usr/lib/python3.9/ctypes/util.py”, line 147, in _findLib_gcc
if not _is_elf(file):
File “/usr/lib/python3.9/ctypes/util.py”, line 99, in _is_elf
with open(filename, ‘br’) as thefile:
FileNotFoundError: [Errno 2] No such file or directory: b’liblibc.a’
Looking into it. I tried
sudo python3 -m pip install scrapy --upgrade
┌─[✗]─[a-man@parrot]─[~]
└──╼ $python3 --version
Python 3.9.1rc1
Looks like a “ctypes bug” issue with Python 3.9.x
yes, i am using latest version with all dependencies downloaded but still its happening
the problem is from python 3.9. It should be fixed in latest version. I’m using rolling testing branch so it is newer than your branch
There is same problem with me. I downloaded xcb and xwayland but it didn’t help. I also updated scrappy module as masmer suggested but it didn’t help too. What should I do?
I’ve downloaded Parrot-xfce-4.11-beta1_amd64.iso and am installing in on VMware. After updating the system (rolling testing?), I’ll see if I can install and test fern-wifi-cracker to verify Python 3.9’s ctypes bug is fixed in the coming Parrot Security 4.11 release.
Thank you. But i have to notice first beta build is still using the old configs of 4.10 which is buggy. You have to remove light-locker. (Latest configs fixed version ofc)
That’s what that pain in the butt was about when it timed-out during the Live installer. Couldn’t log back in to check the install progress. ![]()
Also has an issue with sudo dpkg-reconfigure grub-pc
But I replaced the repository branch from rolling to testing and did upgrades.
As @dmknght said, the issue is fixed in Python 3.9.1 and fern-wifi-cracker is working, at least in the testing branch from which Parrot Security 4.11 will come from.
I feel your pain. Unfortunately i couldn’t spot the bug in time. A dirty trick is switch to tty and kill light-locker and xfce4-screensaver. The package xfce4-screensaver is a fork version of Mate-screensaver which is from old gnome2. So it totally makes sense. Well i don’t know about the grub installation but i’m sure it has issue during upgrade and i had it too.
Offtopic: New XFCE16 looks good and this will be default of new Parrot-xfce release
Is there a fix for the tool or when is the new Parrot out?
Also, is it the only GUI Wi-Fi tool in parrot?
Yes ofc. it is already fixed on testing branch if you check the topic i sent
P/s: ofc the update will be on rolling soon
To be honest, i’d suggest use only aircrack-ng. It supports many kinds of wireless attack.
sudo parrot-upgrade
will now download some upgraded packages like from Python 3.91rc1 => Python 3.91, fixing this issue. Thanks!
i changed my OS now
I use backbox for now,its lightweight good for daily use and has some tools for hacking
Yeah, I finally tricked the 32-bit version of Back Box 6.0 to install on an old Acer Aspire One today and have been setting that up. I’ve been a Back Box enthusiast for a long time, but discovered Parrot Security more to my liking over Back Box, Kali, BlackArch, etc. for pentesting learning. Parrot is cutting edge rolling Debian, Back Box 7 is rather static Ubuntu.
Also experimenting with Demon Linux (from Weaknet Laboratories) today on a VM.
Oh they have new version. I really like their OS. It was weakerthan OS or something like that
Oh wait maybe i’m wrong
Yes, I was searching to see if weakerthan Linux had a x86 version and eventually it led me to their newest Distro, Demon Linux.
Also tried out another Ubuntu-based (18.04) pentest distro Blackbuntu.
And downloaded/tried out nearly every 32-bit Linux (and Windows) I could come across on my oldest netbook. Kali is the only 32-bit pentest distro still supported I could find, but the installer does not like my hard drive controller and can’t see my drive (the live version does however). Tried installing a rolling Debian i686 and adding Kali repo, but it didn’t end up liking that combo during updates. Anyway…
PS: Pentoo also has a 32-bit pentest distro still supported (daily builds), but I couldn’t get it installed on my netbook, don’t know Portage (yet), and I’m concerned that it has links to China.
I’m afraid you have to build 32 bit iso yourself for Parrot (idk if the build still supports 32 bit)
That’s beyond my skill set of course. I did try Parrot Security 4.4 for i386, but as expected the update mirror for i386 no longer exists.
OH well as i checked on repository, the binary i386 is still there
https://deb.parrot.sh/mirrors/parrot/dists/rolling/main/