What version of Parrot are you running?
Parrot GNU/Linux 4.10
What hardware are you running?
CPU: Dual Core Intel Core i7-4558U (-MCP-) speed: 2800 MHz Kernel: 5.7.0-2parrot2-amd64 x86_64 Up: 29m
Mem: 580.9/3940.2 MiB (14.7%) Storage: 80.00 GiB (8.4% used) Procs: 163 Shell: Bash inxi: 3.1.06
What method did you use to install Parrot?
OVA on VirtualBox
Configured to multiboot with other systems?
No
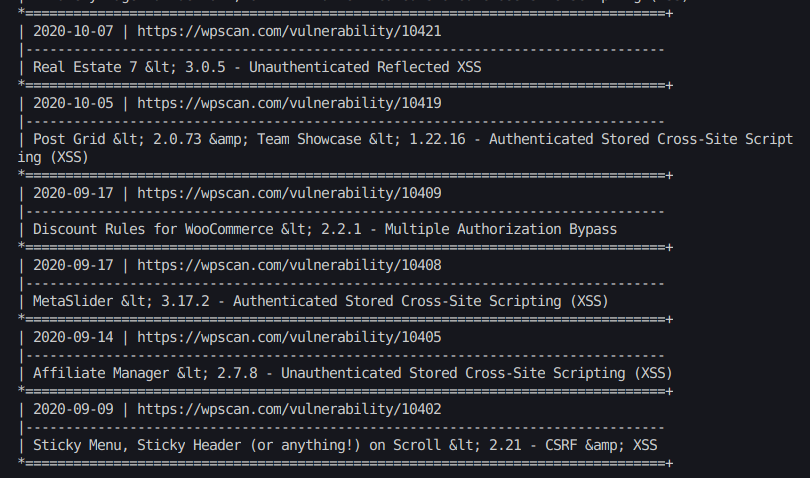
Hello there, new ParrotOS user. I am trying to use pompom, which is installed by default with ParrotOS Security edition.
$pompem -s 'bluekeep'
This returns an error, including suspicious reference to a .onion site:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/urllib3/contrib/pyopenssl.py", line 488, in wrap_socket
cnx.do_handshake()
File "/usr/lib/python3/dist-packages/OpenSSL/SSL.py", line 1934, in do_handshake
self._raise_ssl_error(self._ssl, result)
File "/usr/lib/python3/dist-packages/OpenSSL/SSL.py", line 1664, in _raise_ssl_error
raise SysCallError(-1, "Unexpected EOF")
OpenSSL.SSL.SysCallError: (-1, 'Unexpected EOF')
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/urllib3/connectionpool.py", line 670, in urlopen
httplib_response = self._make_request(
File "/usr/lib/python3/dist-packages/urllib3/connectionpool.py", line 381, in _make_request
self._validate_conn(conn)
File "/usr/lib/python3/dist-packages/urllib3/connectionpool.py", line 978, in _validate_conn
conn.connect()
File "/usr/lib/python3/dist-packages/urllib3/connection.py", line 361, in connect
self.sock = ssl_wrap_socket(
File "/usr/lib/python3/dist-packages/urllib3/util/ssl_.py", line 377, in ssl_wrap_socket
return context.wrap_socket(sock, server_hostname=server_hostname)
File "/usr/lib/python3/dist-packages/urllib3/contrib/pyopenssl.py", line 494, in wrap_socket
raise ssl.SSLError("bad handshake: %r" % e)
ssl.SSLError: ("bad handshake: SysCallError(-1, 'Unexpected EOF')",)
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/requests/adapters.py", line 439, in send
resp = conn.urlopen(
File "/usr/lib/python3/dist-packages/urllib3/connectionpool.py", line 724, in urlopen
retries = retries.increment(
File "/usr/lib/python3/dist-packages/urllib3/util/retry.py", line 439, in increment
raise MaxRetryError(_pool, url, error or ResponseError(cause))
urllib3.exceptions.MaxRetryError: HTTPSConnectionPool(host='j5dtyooqyukedkrl.onion.to', port=443): Max retries exceeded with url: / (Caused by SSLError(SSLError("bad handshake: SysCallError(-1, 'Unexpected EOF')")))
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/share/pompem/core/scrapers.py", line 139, in run
req_worker = RequestWorker(url=url_search, data={'agree': 'Yes%2C+I+agree'},
File "/usr/share/pompem/core/request_worker.py", line 23, in __init__
self._request_session = self._session.post(self._session_url, data=self._data, headers=self._headers)
File "/usr/lib/python3/dist-packages/requests/sessions.py", line 578, in post
return self.request('POST', url, data=data, json=json, **kwargs)
File "/usr/lib/python3/dist-packages/requests/sessions.py", line 530, in request
resp = self.send(prep, **send_kwargs)
File "/usr/lib/python3/dist-packages/requests/sessions.py", line 643, in send
r = adapter.send(request, **kwargs)
File "/usr/lib/python3/dist-packages/requests/adapters.py", line 514, in send
raise SSLError(e, request=request)
requests.exceptions.SSLError: HTTPSConnectionPool(host='j5dtyooqyukedkrl.onion.to', port=443): Max retries exceeded with url: / (Caused by SSLError(SSLError("bad handshake: SysCallError(-1, 'Unexpected EOF')")))
Traceback (most recent call last):
File "/usr/share/pompem/core/scrapers.py", line 28, in _get_results
self._parser(html)
File "/usr/share/pompem/core/scrapers.py", line 188, in _parser
for data in json_data['data']['search']:
KeyError: 'search'
Specifically j5dtyooqyukedkrl[.]onion[.]to. I can’t find much information about this, other than a reference on Threat Crowd.
Can anyone help me understand what the issue might be?