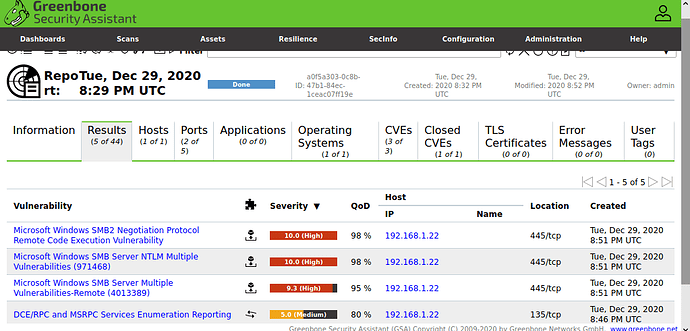
Well i blame wrong suggested command from gvm script. And thank you for your testing time ^^. I guess finally we have reason to keep this gvm.
Oh btw the w3af is a web auditing framework and it was removed years ago. The project is still under maintained but the release has been stopped since 2015. So i’m wondering if you interested in this, maybe you can help us test this project. It would be good if we have other web auditing framework.
Yay! I was worried it would be taken out of Parrot. No problem, I am just a beginner but know enough to use nmap for target scanning, OpenVAS for automated vulnerability analysis of target(s), and a little Metasploit for exploiting those vulnerabilities to gain access.
I’ve ran across that name in the past. I’ve been looking the source over and see several issues:
It apparently uses Python 2. While Parrot has Python 2 available, it doesn’t have the Python 2 pip installer for installing 3rd party libraries.
┌─[✗]─[a-man@parrot]─[~]
└──╼ $python2 -m pip install PyGTK
/usr/bin/python2: No module named pip
┌─[✗]─[a-man@parrot]─[~]
└──╼ $sudo apt-get install python-pip
Reading package lists... Done
Building dependency tree
Reading state information... Done
Package python-pip is not available, but is referred to by another package.
This may mean that the package is missing, has been obsoleted, or
is only available from another source
However the following packages replace it:
python3-pip
Next, the first Python 2 library it requires (for the GUI at least) is PyGTK for GTK+2, whereas Python 3 has moved on to python3-gi (PyGObject Introspection) for GTK+3. The Python 2 PyGTK library was last updated October 25th 2011.
IMO, transitioning w3af and its required library code from Python 2 to Python 3 will require an advanced developer, not a n00b script kiddie who has intermediate Google-Fi skills like me.
I would love to help, but can’t. Sorry. Maybe I can write up something on setting up Greenbone OpenVAS or just answer the easy questions in this Community and the Facebook Parrot OS (Official Group).
But I’m willing to test it for the developers if they are working on updating it. ![]()
http://docs.w3af.org/en/latest/index.html
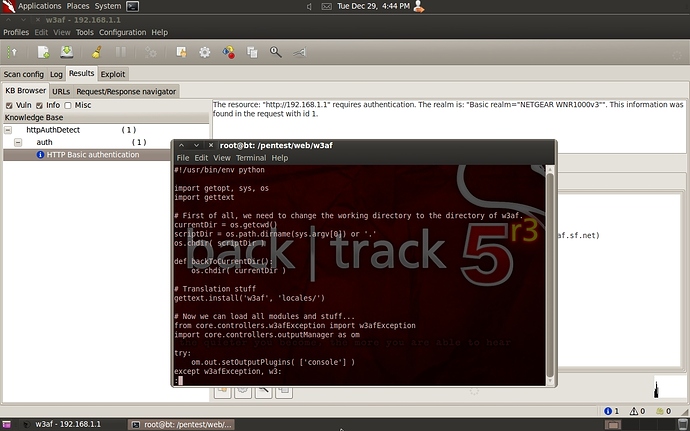
I have the old BackTrack 5R3 iso and will install it in VMware to take a look at the tool.
Ah no a little misunderstood here ![]() i meant maybe we can remove it from pre-installed only. And it will be on cloud version. The gvm will still be on the repository.
i meant maybe we can remove it from pre-installed only. And it will be on cloud version. The gvm will still be on the repository.
Oh i didn’t notice that. RIP! I think Parrot has no choice
I didn’t know what cloud version meant. I thought maybe it was a Docker or AWS version of Parrot. Whew!
BTW: My 12 year old under-powered netbook (N260 Atom processor, 1 GB RAM, 32-bit Kali) is able to scan systems like my other netbook I setup last week running Windows 2008 server (with the firewall off). Pretty cool!
I don’t know for certain about w3af using Python 2, but usually if Python 3 is not mentioned with older Python projects, it’s assumed Python 2. I could not install PyGTK using Python 3’s pip.
I installed BackTrack 5 R3 as a Virtual Box guest and used w3af real quick to scan my router. I’ll probably setup my netbook running Windows Server 2008 to be an old IIS web server and use w3af (and Burp Suite Community?) to play around a bit.
Oh yes that is it. The idea is some tools like gvm, beef XSS must be used on server side. It doesn’t make sense when regular usage is on endpoint side. And i mean in enterprise model, gvm or any vuln assessment system is on standalone server to control vulns inside network. So yeah the idea is making a pre-installed iso for that only.
I got pretty lag Parrot with GVM on inside vmware. I have to provide 4gb ram. 2gb ram wasn’t enough for me.
i checked shebang of w3af and it uses python2. Well project is not bad at all but it has problems like freezy gui and some exception error. I mean w3af is good for web auditing beside gvm for network auditing. Not everybody has burp pro for scan and Zaproxy is just acceptable. And ofc i said audit because it will be used to run, scan, make report and burp / zap is for not only scanning but manual pentesting. It is different usage so that is the idea. Unfortunately i don’t think Parrot can have w3af.
P/s: talk about it, more CMS scanner should be added to Parrot too.
I read somewhere about speeding up OpenVAS by editing some JIT parameter in the PostgreSQL config file. They said that OpenVAS used to be a lot quicker before switching to PostgreSQL 13, but they were able to reduce the scanning time by a lot. I think it was actually disabling JIT in the config file. I’ll track that down and test.
Starting OpenVAS on my netbook running Kali 32-bit takes about 10 minutes of disk thrashing before I can use it. The scan took the usual 20 minutes or so (also about the time experienced by my VirtualBox, VMware, and 2 laptops running Parrot while scanning Metasploitable 2).
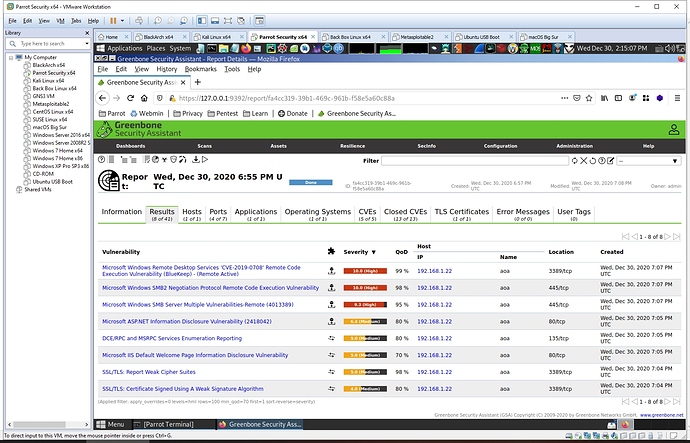
BTW: Last night I installed IIS 7 webserver on my netbook running Windows 2008 Server and used the other netbook to scan it. Many more vulnerabilities found of course. I exported the resulting OpenVAS report in XML for importing into Metasploit. I’ll see what a w3af scan results in. This is fun stuff for a N00b!
Parrot on VMware. OpenVAS report after scanning Windows Server 2008 SP1 with IIS 7 employed, remote desktop services allowed, and firewall off:
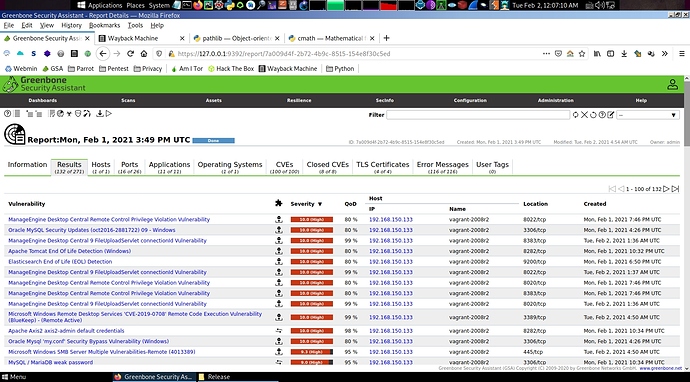
Hm interesting. I’m reinstalling gvm on real machine and i’ll test it with faraday.
P/s: yeah it is completed on real machine. Look like in previous setup, something was wrong during rsync database update and gvm fixed it.
It is cool. I remember few years ago openvas couldn’t detect vulns in metasploitable2. The db has been upgraded so much.
This topic was automatically closed 120 days after the last reply. New replies are no longer allowed.