Open process blah blah… rootkit and hidden processes blah blah… Skipped to the point:
There are some mechanics to detect hidden processes on Linux system. 1 of them is checking procfs. Technical information:
- You can’t see the process information when use
ps - You can’t see procfs folder when do
ls /proc/ - You CAN cd procfs and read data inside the folder because it’s available
- This method is easy to program (it took me 1 hour to create a script. I spent 30 mins to detect a bug that i defined wrong value for a variable).
There are some projects can do that:
-
unhide: written in C (mostly?), available on repository. Dosudo apt install unhide - A project written in Golang, article about it Linux Stealth Rootkit Process Decloaking Tool – sandfly-processdecloak. Link to source code: GitHub - sandflysecurity/sandfly-processdecloak: Sandfly Linux Stealth Rootkit Decloaking Utility
Testing with Diamorphine rootkit
- Some basic commands to use this rootkit Expose hiding processes - Learning Wazuh · Wazuh documentation
- Rootkit source code (compiled okay on Parrot with kernel 6.0): GitHub - m0nad/Diamorphine: LKM rootkit for Linux Kernels 2.6.x/3.x/4.x/5.x (x86/x86_64 and ARM64)
Skipped the build and infect system step
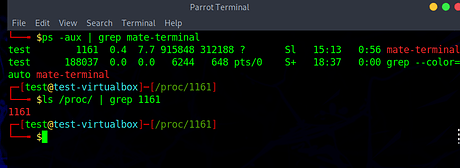
The test process is 1161 which is mate-terminal. We can see the process in both ps and ls /proc/ | grep 1161
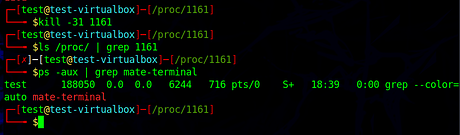
Tell rootkit to hide the process, system can’t see it
However, listing directory is fine
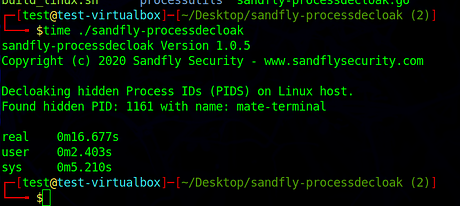
Run simple check with the sandfly-processdecloak, it took about 16 sec to do complete check.
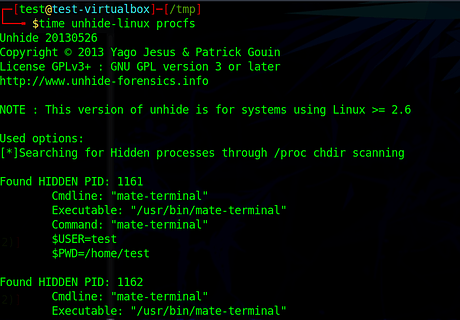
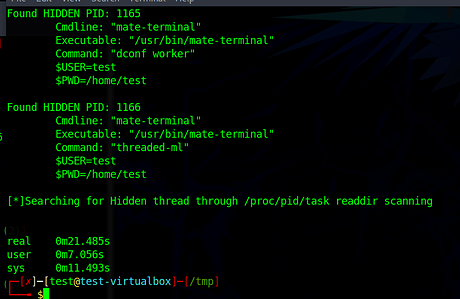
Test with unhide-linux. Problems:
- It requires root permission (dont trust this screenshot. I told the rootkit to give current user root permission)
- False positive
- High CPU usage. The whole system was laggy when it ran
- Slow (it took 21 secs)
My tool, which is ported (I stole the code) of processuncloak src/tools/unhide_procs.nim · main · Nong Hoang Tu / rkcheck · GitLab
Downloaded script inside VM (name’s test)
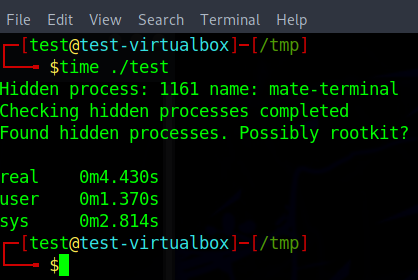
It took < 5 secs to complete check. The whole source code has 64 lines and very easy to read (my code syntax is bad though)