@therealavatar , Odin the All-Father Hello!
It’s quite fun you talk me about Firejail. My first target was to make apparmor and firejail work together correctly. So user and kernel level fully protected.
There is a perfect example of what I wanted to do, Kicksecure’s apparmor profile for torbrowser with firejail.
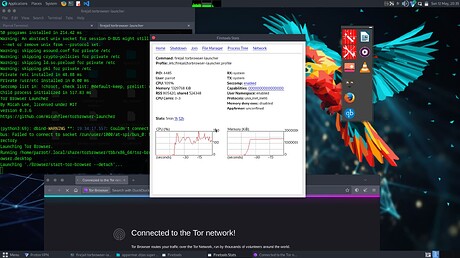
Tor browser without it (not even using firejails.default apparmor profile when starting firejail torbrowser-launcher ) :
Apparmor is unconfied
┌─[parrot@parrot]─[~]
└──╼ $sudo jailcheck
[sudo] password for parrot:
Warning: invalid directory ~/.ssh, skipping...
4485:parrot::firejail torbrowser-launcher
Warning: AppArmor not enabled
Virtual dirs: /home/parrot, /tmp, /var/tmp, /dev, /etc, /bin,
/usr/share, /run/user/1000,
Networking: enabled
┌─[parrot@parrot]─[~]
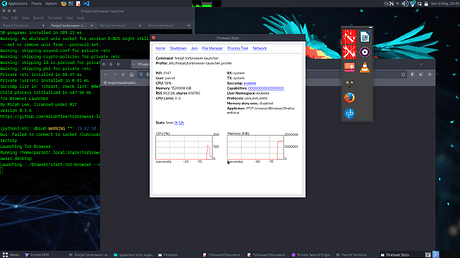
Now with the kick secure profile, started the same way:
6147:parrot::firejail torbrowser-launcher
Virtual dirs: /home/parrot, /tmp, /var/tmp, /dev, /etc, /bin,
/usr/share, /run/user/1000,
Networking: enabled
This is great!
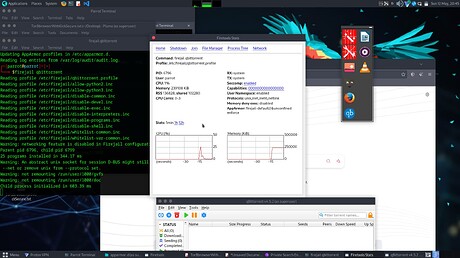
And now… qbittorrent started with firejail qbittorrent
Apparmor UNCONFINED it’s gross
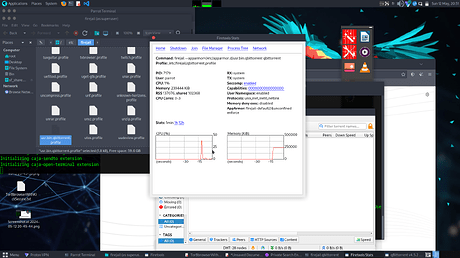
Trying to force it using the correct apparmor profile using firejail --appamor=/etc/apparmor.d/usr.bin.qbittorrent
He don’t care.
May have you the super power to find out how make it work correctly as tor browser with kicksecure apparmor?
I’m probably not good enough, then I was thinking using apparmor +
Tomoyo?
bubblewrap?
chroot?
docker?
Thanks, you are my last hope 
Thanks and I enjoy this thread!